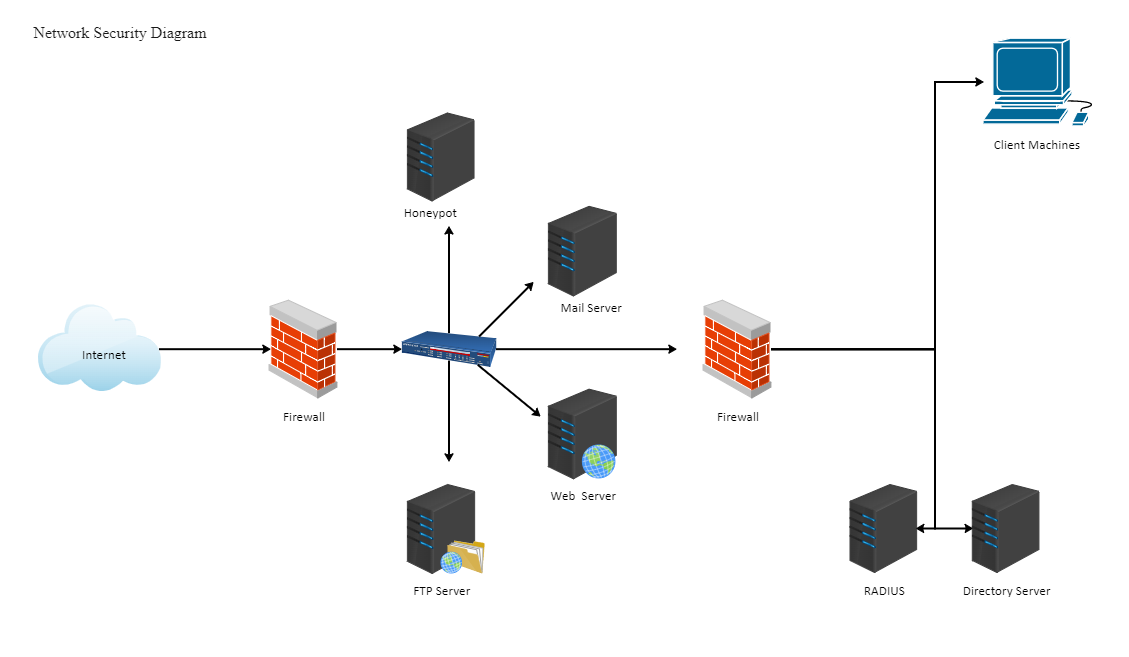
List Types Of Security Methods Used For Computer System . Ddos attacks often rely on botnets — networks of compromised. Here are the most common ones include the following: Below are some of the most. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file.
from www.edrawmax.com
Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Here are the most common ones include the following: Below are some of the most. Ddos attacks often rely on botnets — networks of compromised.
Network Security Diagram EdrawMax Templates
List Types Of Security Methods Used For Computer System Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Ddos attacks often rely on botnets — networks of compromised. Here are the most common ones include the following: Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Below are some of the most. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks.
From www.g2.com
Exploring Network Security (+8 Ways to Protect Your Network) List Types Of Security Methods Used For Computer System Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Below are some of the most. Here are the most common ones include the following: Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Ddos attacks often rely on botnets — networks of compromised. List Types Of Security Methods Used For Computer System.
From www.extnoc.com
What is Network Security? List Types Of Security Methods Used For Computer System Below are some of the most. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Here are the most common ones include the following: Ddos attacks often rely on botnets — networks of compromised. List Types Of Security Methods Used For Computer System.
From www.techtarget.com
Explore 9 Essential Elements of Network Security List Types Of Security Methods Used For Computer System Ddos attacks often rely on botnets — networks of compromised. Below are some of the most. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Here are the most common ones include the following: Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. List Types Of Security Methods Used For Computer System.
From jelvix.com
What Is Database Security Standards, Threats, Protection List Types Of Security Methods Used For Computer System Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Here are the most common ones include the following: Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Ddos attacks often rely on botnets — networks of compromised. Below are some of the most. List Types Of Security Methods Used For Computer System.
From lifelock.norton.com
Password security How to create strong passwords in 5 steps List Types Of Security Methods Used For Computer System Here are the most common ones include the following: Below are some of the most. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Ddos attacks often rely on botnets — networks of compromised. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. List Types Of Security Methods Used For Computer System.
From e-ghl.com
Types of Payment Methods eGHL List Types Of Security Methods Used For Computer System Ddos attacks often rely on botnets — networks of compromised. Below are some of the most. Here are the most common ones include the following: Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. List Types Of Security Methods Used For Computer System.
From blog-tractebel.lahmeyer.de
First steps to implement an ISMS Lahmeyer International List Types Of Security Methods Used For Computer System Below are some of the most. Here are the most common ones include the following: Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Ddos attacks often rely on botnets — networks of compromised. List Types Of Security Methods Used For Computer System.
From inkaikonen.blogspot.com
How To Keep Computer Secure 5 Ways to Keep Your Data Safe and Secure List Types Of Security Methods Used For Computer System Below are some of the most. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Here are the most common ones include the following: Ddos attacks often rely on botnets — networks of compromised. List Types Of Security Methods Used For Computer System.
From www.businesstechweekly.com
5 Essential data security best practices for keeping your data safe List Types Of Security Methods Used For Computer System Ddos attacks often rely on botnets — networks of compromised. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Below are some of the most. Here are the most common ones include the following: List Types Of Security Methods Used For Computer System.
From purplesec.us
Types Of Security Controls Explained List Types Of Security Methods Used For Computer System Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Ddos attacks often rely on botnets — networks of compromised. Here are the most common ones include the following: Below are some of the most. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. List Types Of Security Methods Used For Computer System.
From seeqbasicomputer.blogspot.com
Qbasic Programming Solutions and SLC / SEE Computer Science Questions List Types Of Security Methods Used For Computer System Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Below are some of the most. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Ddos attacks often rely on botnets — networks of compromised. Here are the most common ones include the following: List Types Of Security Methods Used For Computer System.
From pharmakondergi.com
Common Encryption Types Protocols And Algorithms Expl vrogue co List Types Of Security Methods Used For Computer System Below are some of the most. Ddos attacks often rely on botnets — networks of compromised. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Here are the most common ones include the following: List Types Of Security Methods Used For Computer System.
From systemsurveyor.com
Understanding Physical Security Risks System Surveyor List Types Of Security Methods Used For Computer System Ddos attacks often rely on botnets — networks of compromised. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Here are the most common ones include the following: Below are some of the most. List Types Of Security Methods Used For Computer System.
From www.esikai.com.np
पाठ ४ कम्प्युटरका प्रकार (Types of Computer) कम्प्युटर शिक्षा कक्षा ७ List Types Of Security Methods Used For Computer System Ddos attacks often rely on botnets — networks of compromised. Here are the most common ones include the following: Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Below are some of the most. List Types Of Security Methods Used For Computer System.
From www.businesstechweekly.com
5 Essential data security best practices for keeping your data safe List Types Of Security Methods Used For Computer System Here are the most common ones include the following: Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Ddos attacks often rely on botnets — networks of compromised. Below are some of the most. List Types Of Security Methods Used For Computer System.
From www.edrawmax.com
Network Security Diagram EdrawMax Templates List Types Of Security Methods Used For Computer System Below are some of the most. Ddos attacks often rely on botnets — networks of compromised. Here are the most common ones include the following: Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. List Types Of Security Methods Used For Computer System.
From www.csoonline.com
What is application security? A process and tools for securing software List Types Of Security Methods Used For Computer System Below are some of the most. Here are the most common ones include the following: Ddos attacks often rely on botnets — networks of compromised. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. List Types Of Security Methods Used For Computer System.
From www.quality-assurance-solutions.com
Computer Protection Security Guidelines List Types Of Security Methods Used For Computer System Threat actors employ cybersecurity attacks to perform malicious activities against computer systems, devices, or networks. Ddos attacks often rely on botnets — networks of compromised. Below are some of the most. Malware, short for malicious software, is an umbrella term used to refer to a hostile or intrusive program or file. Here are the most common ones include the following: List Types Of Security Methods Used For Computer System.